In March 2018, our good friend and colleague, Kevin Sanders, published a blog post which documented the process of making the UWL Repository accessible from within the Tor network, as an onion service, in order to highlight issues of intellectual surveillance as an impediment to accessing research and scholarly materials.
Thanks to this work, a global audience of users was given the opportunity to access UWL scholarly materials in a way that preserved their intellectual privacy, ensuring neither their ISP nor UWL, as a service provider, would be able to track their personal use of the repository. The following year in November, Kevin took steps to make the University’s flagship open access journal, New Vistas, accessible as an onion service in the same spirit.
Following these activities at UWL, Library Service colleagues expressed their desire to see Kevin’s proof-of-concept maintained into the future.
In practical terms and in light of Tor’s roadmap to prioritise a more secure scheme for onion services, this involved not only recreating the equivalent onion services at more permanent locations but upgrading them to conform to the preferred (v3) scheme above. These links (which are hashes of the public keys for each of the onion services) continue to use the top level domain (TLD) .onion but can be distinguished by their much longer 56-character length:
UWL Repository:
http://jibtvgs3aedcoclau7ahhqymrk4ut3xcgpccgx3z5gpeoemmpodnhcqd.onion
New Vistas journal:
http://av5idj7ggxj4gskx7ae7wwcoewulxumwp4m5mlwoybdqhj6s7wycajyd.onion/newvistas
In addition to this, library service colleagues decided to make use of the onion-location feature that allows standard domain addresses accessed within Tor (for eg. https://repository.uwl.ac.uk) to signpost to their .onion counterparts.
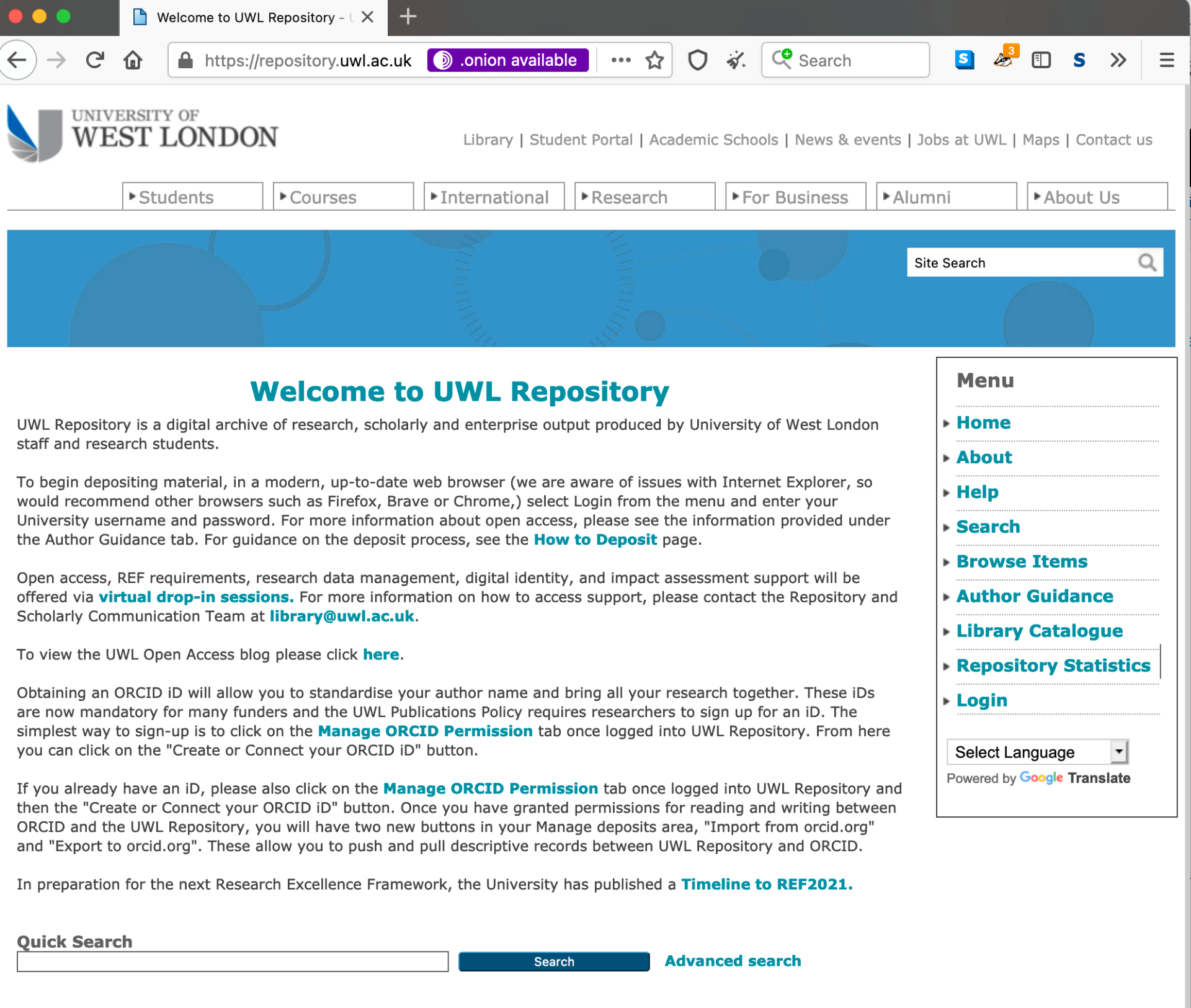
By configuring the onion-location feature and sharing the onion service details as we have in this blog post we aim to contribute towards the ongoing conversation about the role of intellectual privacy in opening up research as well as introduce opportunities for users to access online research content with a greater degree of anonymity. Depending on the end goal, highlighting onion service details in this way can also be useful as onion services are not indexed in search engines in the typical way that clear net websites are.
On the subject of the onion-location feature, the Tor Project have said, ‘for years, some websites have invisibly used onion services with alternative services, and this continues to be an excellent choice. Now, there is also an opt-in mechanism available for websites that want their users to know about their onion service that invites them to upgrade their connection via the .onion address’.

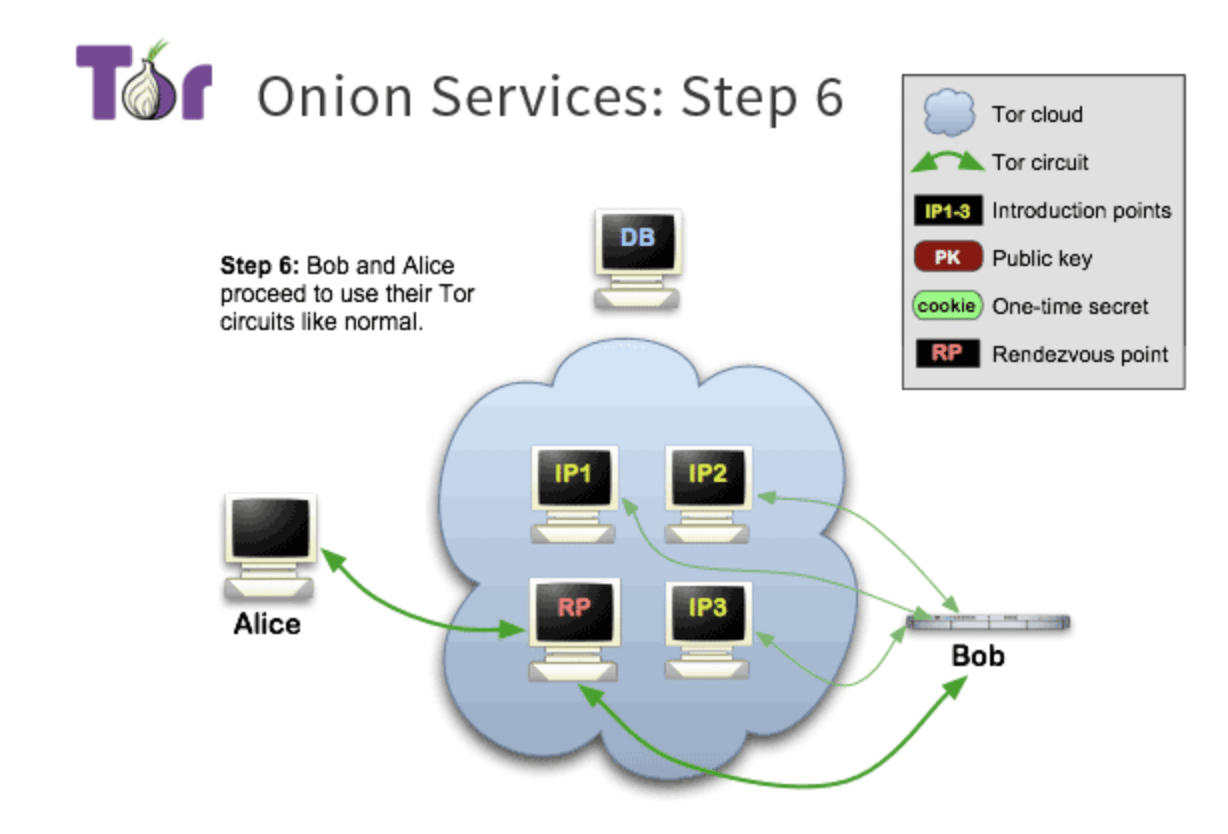
So how are onion services different to a Tor relay in the network?
You may already be familiar with Tor, the browser and volunteer network of Tor relays. Tor relays are part of a decentralised public infrastructure system where Tor users’ traffic is routed from one relay to the next, adding a layer of encryption each time, until it reaches the exit node where it leaves the network and contacts the destination server via an unencrypted link. This means that the final stretch of traffic is more vulnerable to surveillance and could be targeted by an organisation or bad actor monitoring or even running an exit node.

Onion services don’t operate like a series of conventional Tor relays in this regard. Instead, a user connects to an onion service (formerly known as a hidden service) thanks to a series of “handshakes” that help to establish a “rendezvous point” within Tor that supports authentication between users and services without disclosing their network identities (IP addresses). This means that a user’s interaction with an onion service can never be surveilled by the monitoring of Tor exit nodes, for instance. It also means that someone hosting a website can protect the location of their server, allowing both points of a connection to be anonymised. This has the advantage of creating a metadata-free environment between user and service (with the usual caveat that users and services should continue to observe their threat models and avoid identifying themselves by other means, such as by signing their name on a blog post or logging into a service that uses their real name).
You can read more about the wider benefits of onion services with regards to censorship circumvention and network sustainability here.
To access an onion service, you’ll need to access it through the Tor browser. It’s a modified version of Firefox that’s configured to connect to sites through the Tor network.
Download the Tor browser from the Tor project’s website It’s available for Windows, Mac, Linux, and Android.
Acknowledgements:
We would like to give special thanks to the following people for their past and present support and curiosity in helping to configure and maintain the above onion services: Andy Byers, Ed Oakley, Andrew Preater, Murray Royston-Ward, Mauro Sanchez and Kevin Sanders. We would also like to acknowledge the tireless advocacy of Alison Macrina whose campaigns and influence on intellectual privacy issues are unmatched. You can find out more about her important work here: https://libraryfreedom.org/